Koosa 

Declarative Swift framework for Attributed Role-based Access Control management
Check out this blog post for full explanation and more details: Access Control Management with Swift
Example
Usage:
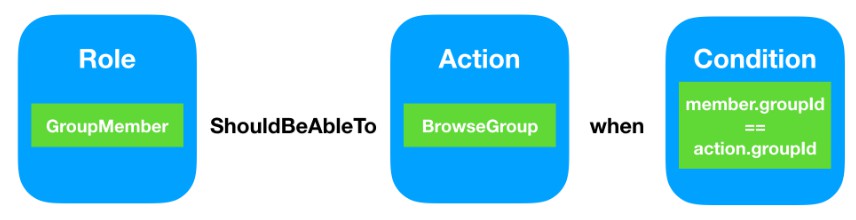
- Start by mapping each role in your requirements to a protocl that extends to prtocol
Roleor a protocl that extends it. Note that you can model role heirarchy using protocl inheritance.
protocol GroupMember: Role {
var groupNumber: Int {set get}
}
protocol GroupAdmin: GroupMember { }
- Model your actions into classes/strcut that conforms to protocl
Action.
struct BrowseGroup: Action {
let group: Group
init() { // required default initializer
group = Group(groupNumber: -1, isPublicGroup: false) // default froup
}
init(group: Group) {
self.group = group
}
}
- Use role protocls to create concrete role classes.
class GroupAdminUser: User, GroupAdmin {
var groupNumber: Int
init(name: String, age: Int, groupNumber: Int) {
self.groupNumber = groupNumber
super.init(name: name, age: age)
}
override required init() {
self.groupNumber = -1
super.init()
}
}
- Add the policies.
GroupMemberUser.shouldBeAbleTo(BrowseGroup.action).when {
guard let groupMember = $0 as? GroupMember,
let browseAction = $1 as? BrowseGroup else { return false }
return groupMember.groupNumber == browseAction.group.groupNumber
}
GroupAdminUser.shouldBeAbleTo(DeleteGroup.action).when {
guard let groupAdmin = $0 as? GroupAdminUser,
let deleteAction = $1 as? DeleteGroup else {
return false
}
return groupAdmin.groupNumber == deleteAction.group.groupNumber
}
_ = SuperAdminUser.shouldBeAbleTo(BrowseGroup.action)
- Now you can validate if any user can do any action.
let member1 = GroupMemberUser(name: "member1", age: 18, groupNumber: 1)
let admin2 = GroupAdminUser(name: "admin2", age: 22, groupNumber: 2)
let group1 = Group(groupNumber: 1, isPublicGroup: false)
let group2 = Group(groupNumber: 2, isPublicGroup: false)
member1.can(BrowseGroup(group: group1) // true
member1.can(BrowseGroup(group: group2) // false
admin2.can(BrowseGroup(group: group1) // true: GroupAdmin inherits BrowseGroup permission from GroupMember
admin2.can(DeleteGroup(group: group2) // true
admin2.can(DeleteGroup(group: group1) // false
Installation
Koosa can be installed using CocoaPods
use_frameworks!
pod 'Koosa'
License
MIT