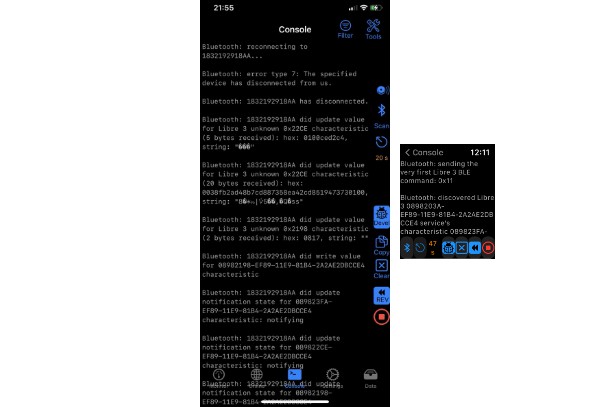
Since the FreeStyle Libre 2 / 3 glucose sensors are Bluetooth Low Energy devices, I am trying to leverage their capabilities to implement something new compared to the traditional apps:
- a universal SwiftUI application for iPhone, iPad and Mac Catalyst;
- an independent Apple Watch app connecting directly via Bluetooth;
- scanning the Libre directly via NFC and exploring its internals;
- using both online servers and offline methods for calibrating just like the temperature-based vendor algorithm;
- showing for comparison the HealthKit and Nightscout data shared with other apps;
- varying the reading interval instead of the usual 5-minute one;
- a detailed log to check the traffic from/to the BLE devices and remote servers.
Still too early to decide the final design (but I really like already the evil logo ?), here there are some recent screenshots I tweeted:
Hello Libre 3
The project started as a single script for the iPad Swift Playgrounds to test the workings of the several troublesome BLE devices I bought, mainly the Bubble and the MiaoMiao. It was then quickly converted to an app when the Libre 2 came out at last by using a standard Xcode template: it should compile fine without external dependencies just after changing the Bundle Identifier in the General panel of the Targets settings and the Team in the Signing and Capabilities tab of Xcode — Spike and xDrip4iO5 users know already very well what that means… ?
I am targeting only the latest betas of Xcode and iOS. The new async / await and actors introduced in Swift 5.5 and iOS 15 probably would require a total rewrite of DiaBLE’s foundations, as well as the enhanced Gen2 protocols adopted by the recent Libre 2 Sense/US/CA/AU which haven’t been reversed yet.
Please refer to the TODOs list for the up-to-date status of all the current limitations and known bugs of this prototype.
Note: the exploitation which allows to reset and reactivate a Libre 1 is well known to the Vendor and was unveiled already during BlackAlps 2019 and in PoC||GTFO 0x20.
Credits: @bubbledevteam, @captainbeeheart, @cryptax, @dabear, @ivalkou, @keencave, LibreMonitor, Loop, Marek Macner, Nightguard, @travisgoodspeed, WoofWoof, xDrip+, xDrip4iO5.